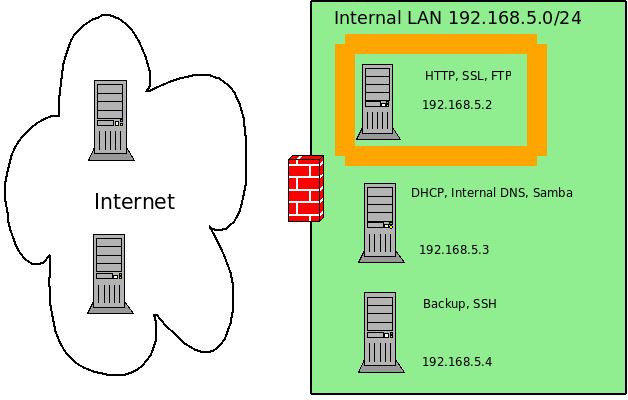
Set up the Firewall
The ufw firewall, Uncomplicated Firewall, is a little tricky. This example is also complex in that the internal network has one server that will be accessed from the Internet. As a result all internal machines must have firewalls to protect them. Now, certainly this is not the best set up as a DMZ would be better but the example is provided as this is the way many organizations are set up, regardless of security issues.
One thing that is important to recognize in regard to the UFW firewall is that there are already several common rules that are configured into the firewall immediately. One of those is the state rules that provide for any RELATED or ESTABLISHED connections. This means that if you connect to a web server from a machine it will allow the information you requested from the web server to return based on the fact that the local machine established the connection and the returning information was related to that request.
Protocols and Ports you will need open:
SSH (22)
FTP (21)
WEB (80)
Secure WEB (443)
Samba (139,445)
DNS (53)
DHCP (67,68)
ufw allow http
Rules updated
# ufw allow proto tcp from 192.168.5.0/24 to any port 22
Rules updated
# ufw enable
Command may disrupt existing ssh connections. Proceed with operation (y|n)? y
Firewall started and enabled on system startup
ufw allow ftp
ufw allow proto tcp from 192.168.5.0/24 to any port 139
ufw allow proto tcp from 192.168.5.0/24 to any port 445
# ufw status
Status: loaded
To Action From
– —— —-
21/tcp ALLOW Anywhere
80/tcp ALLOW Anywhere
445/tcp ALLOW 192.168.5.0/24
139/tcp ALLOW 192.168.5.0/24
443/tcp ALLOW Anywhere
22/tcp ALLOW 192.168.5.0/24