Install and Configure Saslauthd
Sasl stands for Simple Authentications and Security Layer. This is the application to use for SMTP AUTH.
Version 2.3, and greater of Postfix supports SMTP AUTH through Dovecot SASL.
Ubuntu Mail server Course
Secure Connections
Postfix with TLS
Dovecot with Sasl
SMTP AUTH
Secure Client
Install saslauthd
sudo apt-get install libsasl2 libsasl2-modules sasl2-bin
The mail server postfix does a chroot so it can’t communicate with saslauthd. As a result you must make these modifications.
rm -r /var/run/saslauthd/
mkdir -p /var/spool/postfix/var/run/saslauthd
ln -s /var/spool/postfix/var/run/saslauthd /var/run
chgrp sasl /var/spool/postfix/var/run/saslauthd
adduser postfix sasl
You will need to edit saslauthd found in /etc/default/saslauthd.
Set the daemon so it with start with this setting:
START=yes
Change the location of saslauthd to the chroot environment of postfix by changing the OPTIONS..
OPTIONS=”-c -m /var/spool/postfix/var/run/saslauthd”
Now set saslauthd so it will use the shadow file.
saslauthd -a shadow
Once you change the location of saslauthd you will not be able to use the testsaslauthd command.
The /etc/postfix/sasl/smtpd.conf file looks like this:
pwcheck_method: saslauthd
mech_list: PLAIN LOGIN
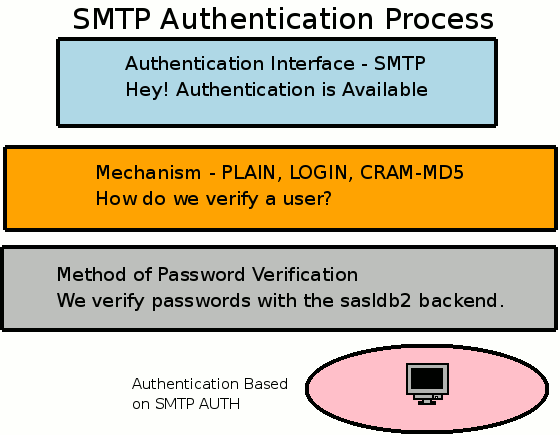
Once you have this in place you are able to use SMTP Authentication. In the example you can see that SMTP Authentication has three parts; the authentication interface, the mechanism and the method of verification. Each of these parts has many options, thus the massive confusion that surrounds this. In the example for this tutorial the mechanism is PLAIN and the method of verification is dovecot.
Remote Client Using TLS and SMTP AUTH
Here are log examples of what you should see when a remote user connects with TLS and SMTP AUTH. You can see in the process the sasl connection and verification as well as the TLS connection.
Oct 28 13:25:26 ub910s postfix/smtpd[5197]: connect from unknown[192.168.5.103]
Oct 28 13:25:27 ub910s postfix/smtpd[5197]: 07A0B5F9F: client=unknown[192.168.5.103], sasl_method=PLAIN, sasl_username=mike
Oct 28 13:25:27 ub910s postfix/cleanup[5203]: 07A0B5F9F: message-id=<4AE898CA.6060205@example.com>
Oct 28 13:25:27 ub910s postfix/qmgr[5193]: 07A0B5F9F: from=<mike@example.com>, size=507, nrcpt=1 (queue active)
Oct 28 13:25:27 ub910s postfix/smtpd[5197]: disconnect from unknown[192.168.5.103]
Oct 28 13:25:27 ub910s dovecot: imap-login: Login: user=<mike>, method=PLAIN, rip=192.168.5.103, lip=192.168.5.98, TLS
Oct 28 13:25:28 ub910s postfix/smtp[5204]: 07A0B5F9F: to=<some_email@gmail.com>, relay=gmail-smtp-in.l.google.com[209.85.216.20]:25, delay=1.7, delays=0.06/0.03/0.63/0.94, dsn=2.0.0, status=sent (250 2.0.0 OK 1256757929 40si3632867pxi.87)
Oct 28 13:25:28 ub910s postfix/qmgr[5193]: 07A0B5F9F: removed
Network Port Check
By running the command netstat you will be able to check to see if your server is listening on the correct ports. You will want port 993 for IMAPS, port 25 for your TLS connection to send mail and port 22 is there for an SSH connection to work on your server.
netstat -aunt
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:993 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN
If you are interested in the Postfix Manual you can purchase for $34.95 which illustrates many more options with Postfix.

{ 1 comment }
Or… If you already installed dovecot, use dovecot’s SASL. Of course, dovecot-postfix package would set this automaticaly for you
{ 1 trackback }