Create a Passive Host Check Test
It is important that you get a test script working correctly before you get too excited about putting together a real script as you want to understand the process and work out any issues before you start writing scripts.
Here is a simple script for sending information about the state of the server to the Nagios server. Note the path is for a CentOS server so adjust yours as needed and you can see the host name is nagpass and the Nagios server IP is 192.168.5.50. All of these must be adjusted to your network. The script is only intended to show you how to communicate to the server and view the information on the web interface.
#!/bin/sh
# Passive Host Check Test Script
CFG=”/etc/nagios/send_nsca.cfg”
CMD=”nagpass;0;Host Status”
/bin/echo $CMD | /usr/sbin/send_nsca -H 192.168.5.50 -d ‘;’ -c $CFG
exit 0
CFG is a variable that contains the path to the send_nsca.cfg file. This file of course must contain the password and encryption type for communicating with the Nagios server. Remember, the password on the client must be the same password on the server so they can communicate. See the Nagios server set up for passive checks if this is unclear.
The CMD variable is a pre-configured message that will be send via send_nsca. The host message contains the hostname of the client (nagpass), the status “0” which indicates the server is up and a text message.
The CMD variable is piped in to the send_nsca command with the Nagios server indicated by the “-H 192.168.5.50”. Change the IP or hostname for your Nagios server. The delimiter is indicated by the “-d ‘;’” which shows that it is the semi-colon and finally the configuration file is sent using the CFG variable.
Create a directory on your client server for all of the scripts you will end up writing so they are in one place. Save the script above as host.sh and chmod 755 host.sh to make it executable. Then run the script, making sure your send_nsca.cfg file contains the same password and encryption type as on the Nagios server.
sh host.sh
Here is the response you should see on the Nagios server in the /var/log/messages. Note the indication that xinetd is listening for the nsca and that the second line indicates that it is a host check and the information from the client has been transferred.
xinetd[3685]: EXIT: nsca status=0 pid=22238 duration=0(sec)
nagios: EXTERNAL COMMAND: PROCESS_HOST_CHECK_RESULT;nagpass;0;Host Status
Now testing the passive host check use the status of “0” the first time on the client and run the script you should see this on the web interface.
![]()
Then change the status to “1” and you should see an indication that the server is down on the web interface.
![]()
Here you can see that flapping is detected. You can stop flap detection with this setting in the /etc/nagios/objects/hosts.cfg.
define host{
use linux-box
host_name nagpass
address 192.168.5.91
active_checks_enabled 1
passive_checks_enabled 1
flap_detection_enabled 0
}
As you change states of the host for testing you can see a summary by opening the host on the web interface and choosing the availability report. Here is an example.
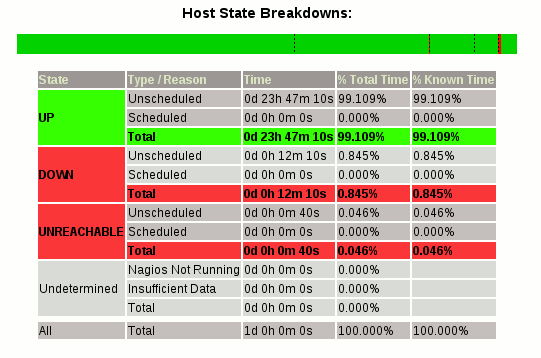
At this point you have completed the process of using a test script to change states for a host on the Nagios server using passive checks.
Check External Commands on Nagios Server
At the command line on the server verify that it will accept commands on the external interface. If this does not work do not go any further until you solve it as if it does not work on the local Nagios server it sure will not work from the clients.
echo “['date +%s'] PROCESS_HOST_CHECK_RESULT;nagpass;2;test” > /var/nagios/rw/nagios.cmd
View /var/log/messages on Nagios Server
If you see something similar you can go to the next step and start working on the client.
Sep 10 16:19:58 fw3 nagios: EXTERNAL COMMAND: PROCESS_HOST_CHECK_RESULT;nagpass;2;test
Sep 10 16:20:03 fw3 nagios: PASSIVE HOST CHECK: nagpass;2;test

{ 1 trackback }